Artikel uit SDN 145
Since security is becoming an increasingly important topic nowadays, I figured.. Why not write an article about it? In this article I am going to explain how you can remove all important (generated) secrets, such as connection strings, access keys, and more from your appsettings files. Instead, we’re going to import them straight into the Key Vault as soon as they roll out of the infrastructure as code (IaC) templates.
Assumptions
Before we continue, I want to define some assumptions. These are the things I expect you have already set up.
- An Azure environment + credits
- You have a Web App or Function already hooked up to Azure App Config + Azure Key Vault
- You are currently deploying your IaC with Bicep
If you don’t have Azure App Configuration set up yet, visit the Azure App Configuration documentation page, or take a look at some examples provided by Microsoft.
If you need an introduction to Bicep, please take a look at this introduction on Microsoft Learn, or consider buying my colleague Eduard Keiholz his book about Azure Infrastructure as Code.

Okay, let’s dive into the Bicep templates. I’d assume your master template looks something like this. There should at least be a resource or template for an App Service, an App Configuration and a Key Vault. Take a look at Example 1. In this article I will not explain how to set up access control between these resources.
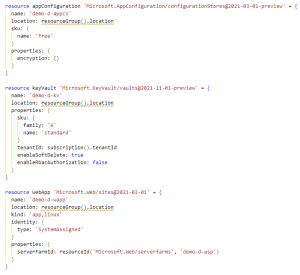
Example 1 – application.bicep (part 1)
Adding a storage account
For example, you decide you want to add a storage account to store some pictures and documents uploaded by your users. You don’t want your developers throwing the access keys around, since the storage account contains sensitive data. The access key should be added to the Key Vault, without you (the developer) ever knowing what the value is.
First, we create a storage account using Bicep. We can then access the access key by using the code on the last line of Example 2. This is the value that we want to add to our Azure Key Vault.
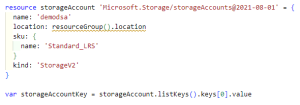
Example 2
Adding the value to Key Vault
I have to admit this took the most time. Lucky for you, I invested the time so you don’t have to! I’ve created a simple template that allows you to add a single key-value pair to your Key Vault. You just need to provide the keyVault name, key, and value.
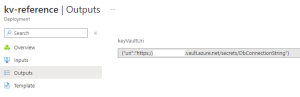
The important lesson-learned is at the bottom of Example 4. Take a look at ‘var keyVaultRef’. Whenever we’re adding a KeyVault reference to Azure App Configuration, Azure requires it to be in an object with a uri property. If you forget this object, your reference to Key Vault will not work and your application can crash. As you can see in Example 3, the first reference is invalid. The other two are correct. You can copy-and-paste the template in Example 4 to your own project.
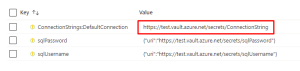
![]()
Example 3
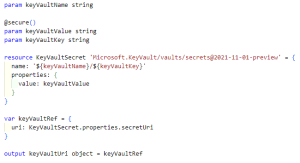
Example 4 – secrets.bicep
Preventing potential security risks
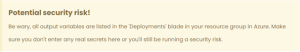
Potential security risks arise when you starting using templates to create your Azure resources in. I get that you don’t want to put all your Azure resource creations in one single file. That would become a total mess on bigger projects. However, when you want to output a secret variable back to your main template, these variables show up in your Outputs blade in Azure.
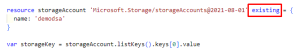
Fixing this issue is actually quite simple. In the template that we want to access the secret, we can reference this resource using the ‘existing’ keyword (Example 6). We can then retrieve the keys without passing them back through the output variables.
This security risk only occurs when outputting variables back to the template they’re called from. However, when you need to pass values on to the templates you want to use, these also show up in Azure under the Inputs blade. Luckily, Bicep already has you covered. We can simply add a ‘@secure()’ above the parameter, and the variable won’t show up in your Inputs blade anymore (Example 4).
Example 5
Example 6
Adding the Key Vault reference to Azure App Configuration
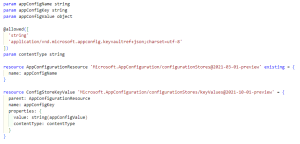
Now, for the final part. We’re going to add our reference to App Config. With the following template, we can decide whether to add a normal string value, or a key vault reference to our App Configuration. You can copy-and-paste Example 7 into your own project.
Example 7 – singleKeyValue.bicep
How will it look when everything is put together?
In Example 8, I will show you the code that we can add to Example 1 to make it complete. You can start expanding this simple example in your own project. You’ll get rid of your secrets in no-time! I hope you enjoyed reading my article and that I inspired you to start implementing this into your own projects!
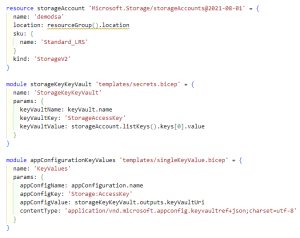
Example 8 – application.bicep (part 2)
 SDN – Software Development Network SDN – Software Development Network – De SDN verenigt software ontwikkelaars, architecten, ICT managers, studenten, new media developers en haar businesspartners met algemene interesse in alle aspecten van Microsoft en .NET.
SDN – Software Development Network SDN – Software Development Network – De SDN verenigt software ontwikkelaars, architecten, ICT managers, studenten, new media developers en haar businesspartners met algemene interesse in alle aspecten van Microsoft en .NET.